Avoiding Phishing Attacks
So, what is phishing and how do I avoid it?
Phishing is an attack that attempts to steal user data, such as log in credentials, by getting you to reveal personal information such as passwords or even bank information. The phisher does this by impersonating a trusted entity, this often misleads a victim into opening an email, instant message, or text message. The recipient is then often tricked into clicking a malicious link which can lead to the installation of malware, the hijacking of the system as part of a ransomware attack or the revealing of sensitive information.
If you are ever unsure about a sketchy email or unusual request, please contact our support team directly on
061 375 140 or via support@itsystems.ie.
Eye-spy with my little eye…
How to spot a phishing attempt
Phishing is a popular form of cybercrime because of how effective it is. It is easy to quickly click a link without paying too much attention. Phishing attacks have become increasingly sophisticated over the past number of years, cybercriminals are even finding ways to emulate your schools email portal or website.
Here are some ways to recognise a phishing email.
Ain’t nobody got time for that…
1. Urgent call to action and threats.
If you receive an email or message that claims that you must perform an action such as a returning a call or opening a link immediately, it is likely that it is a phishing attempt. Cyber criminals create a false sense of urgency to pressure the recipient into clicking a link without looking or seeking further advice. If you are ever unsure, take a moment to pause and look carefully at the message.
Keep an eye out.
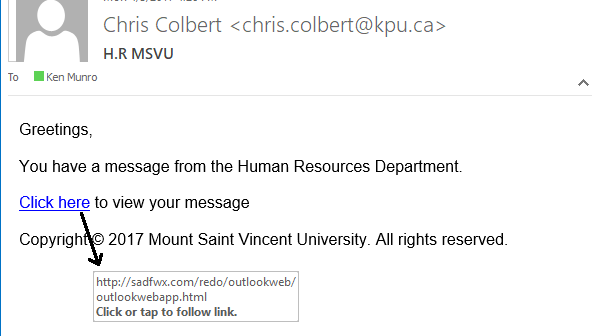
2. Subtle Errors in Email Domains
If the email claims to be from a large enterprise such as Microsoft but it is being sent from an email domain like “Gmail.com” or “microsoftsupport.wu” it is highly likely to be a phishing attempt. It important that you keep an eye for more subtle misspelling of legitimate domains such as 1tsystems where the “I” is replaced by the number “1”. Another very clever example is rnicrosoft.com, where the “m” has been replaced by an “r” and a “n”. These are common tricks of scammers that can be easily missed by an unsuspecting or busy user.
Why so suspicious?
3. Suspicious Links
If you suspect that an email message is a scam, do not open any links or attachments that you see. Instead, hover your mouse over, but do not click the link. Hovering your mouse over a link will show you directly where the link plans to redirect you. It is especially important that you look at this link address or URL very closely as it may help you to determine if this is a phishing attempt.
Staying Alert.
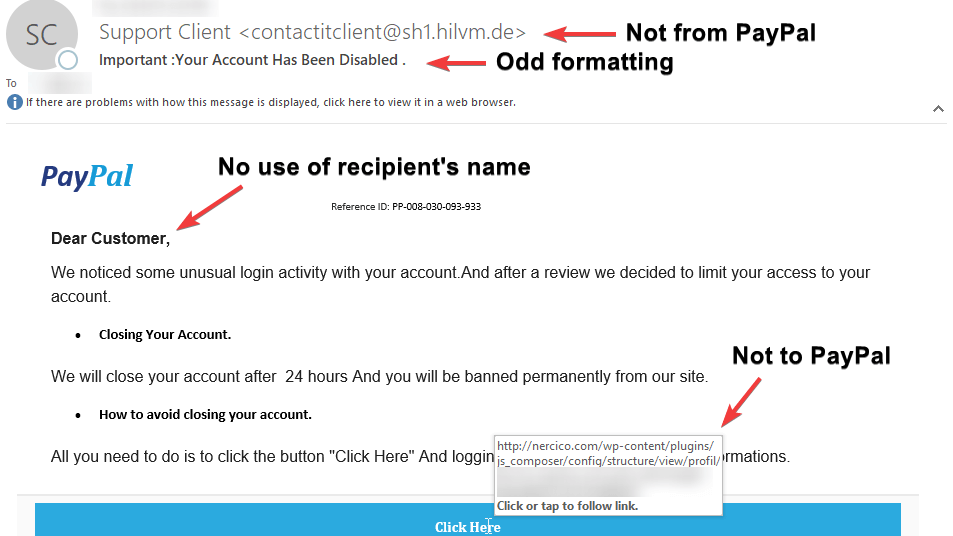
4. Sender Unknown
While it is not unusual to receive an email from someone for the first time, it is important to be aware that it could be a sign of phishing. If you get an email from a name that you do not recognise or if it flagged by outlook as a new sender, take a second to examine it extra carefully.
Spell Check Required.
5. Bad spelling & Grammar
Large companies pride themselves on only sending out high-quality and professional content. If an email has obvious spelling or grammatical errors, it is a massive red flag! This may be due to poor translation from a foreign language or a calculated attempt to avoid filters that are in place to block these very attacks.
But, why?
6. Why did you receive the mail?
If you are are in contact with an organisation on a regular basis, they will address you directly. Keep an eye out for generic greeting such as “Dear Sir or Madam” as this is a strong indicator that it is not who it seems to be. In the example below, the link will redirect you to an unknown provider.
Knock, Knock…
7. Who is it?
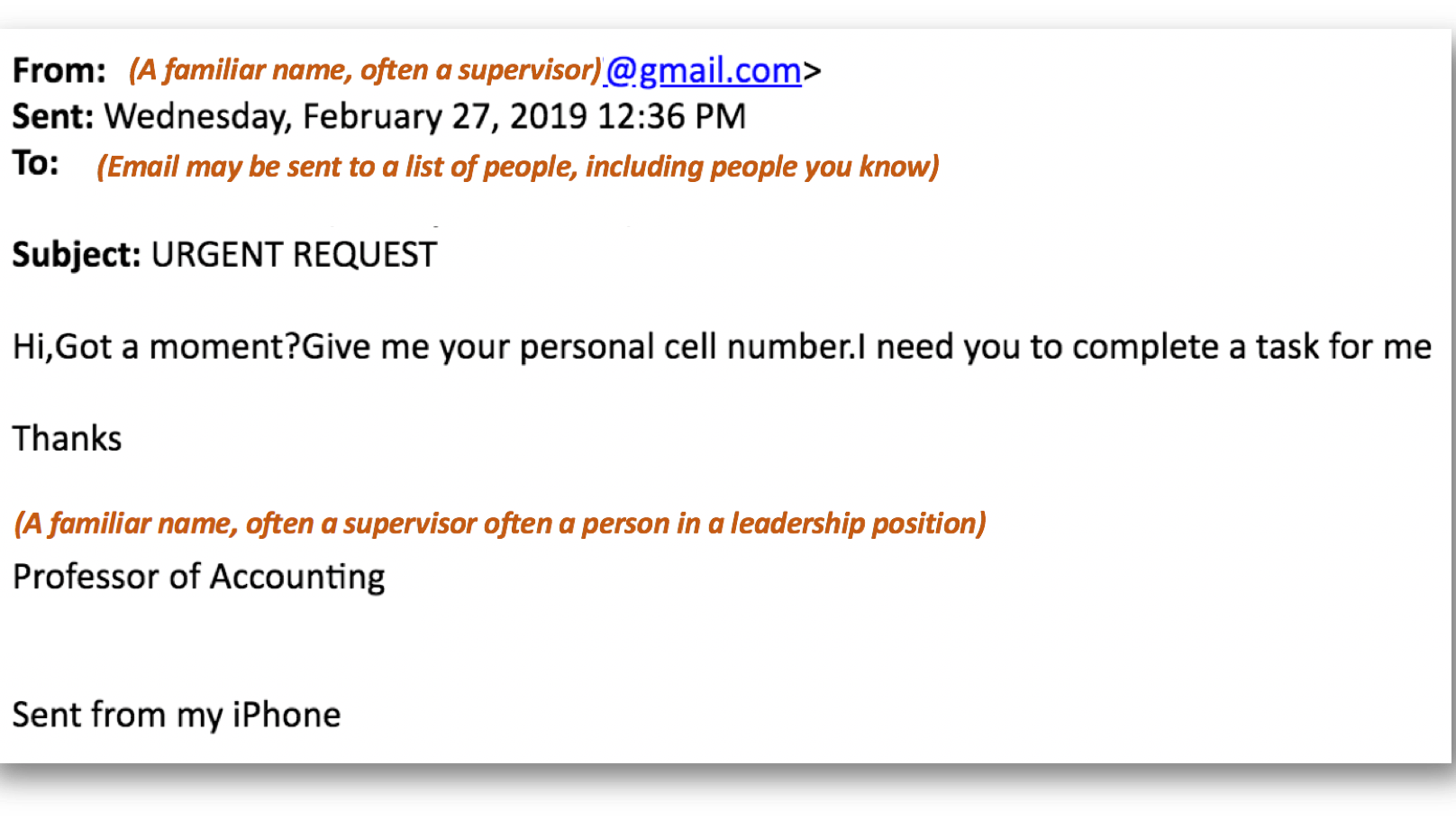
Hackers often use your own email address as the From: address, it is unlikely you sent yourself an email looking for information. Often a hacker will add the name of someone you trust to the From : part of the email. e.g. email might say it is from “My Friend” with an email address myfriend@2345fvvkju.gmail.com or similar. Ofter you will miss the @2345fvvkju. part and only see the “My Friend” part of the address and your mind ignores the other unexpected part. This is simply a trick that hackers use to fool you into thinking the email is legitimate.
Dear Sir/Madam,
8. Generic Greetings
If you are are in contact with an organisation on a regular basis, they will address you directly. Keep an eye out for generic greeting such as “Dear Sir or Madam” as this is a strong indicator that it is not who it seems to be. In the example below, the link will redirect you to an unknown provider.

Get ahead of the game with IT Systems
How do I protect myself from Phishing attempts?
It is important to note that there are ways that you can protect yourself against phishing attempts. Here are a few measures that you can take to keep your organisation safe.
Time to limit access
1. Enable Geographical Restrictions
Almost all malicious attacks originate from locations outside of Ireland. By limiting access from external addresses to only those from known Irish addresses you virtually eliminate most sources of direct attacks.
Microsoft Defender Licencing
2. Get Microsoft Defender Licencing
Microsoft Defender for Office 365 is a cloud-based email filtering service that assists in protecting your organisation from advanced phishing attempts. Microsoft Defender licencing can be added to your existing licences to give you that extra piece of mind.
Dear Sir/Madam,
3. Set-Up Multi-Factor Authentication
Multi Factor Authentication (MFA) is an authentication method that requires the user to provide two or more methods of verification in order to access a resource such as an email account, online account, or a VPN. Instead of asking for a username and password, MFA requires one or more additional verification factors. Therefore, decreasing the likelihood of a successful cyber-attack. Multi-Factor Authentication will boost your school’s security by requiring the users to identify themselves by more than just a username and password.
Raising Awareness with Staff
4. Run awareness sessions with all staff
Run regular briefing sessions with staff to educate them about cybersecurity and show them how they can spot obvious attempts to trick them into aiding an attacker.
Dear Sir/Madam,
5. Replace built in Windows 10 Defender with new Defender for Endpoint
Microsoft Defender for Endpoints is Microsoft’s latest update to the built in Defender that comes with Windows 10 & Windows 11. It is a centrally managed system providing visibility across all of your systems and provided Anti Virus, Anti Malware and also a new AI backed Intrusion Protection system that analyses how your computer is working and prevents unusual activity from taking place. This helps to prevent malicious software from encrypting your system or exploiting it and stealing data.
Raising Awareness with Staff
6. Configure you email system to reject unauthenticated email systems
By disabling older forms of authentication on your email system and by adding authentication records to your email system it is possible to reject emails from systems that are not properly identified on the Internet, this will help to reduce the amount of inbound phishing attempts as these usually come from unauthorised email servers.
Our final thought!
What do I do if I receive a phishing email?
It is important to trust your gut feeling. If you receive an email, message, or call that you are just not too sure about, do not click it. Ring our support line immediately on 061 375 140!
Have a question about Cybersecurity? Get in Contact!






Recent Comments